In the world of industrial automation, the S7 protocol doesn't make headlines — but it quietly powers a massive portion of the OT landscape, especially where Siemens devices are in play.
Yet from an Asset and Security Management (ASM) lens, S7 represents both a strength and a surface of vulnerability.
✅ The Pros: Why S7 Makes Asset Visibility Easier
From a security operations perspective, S7 offers certain operational and monitoring benefits:
- Vendor Consistency: It's ubiquitous in Siemens environments, aiding standardization and simplifying asset classification.
- Detectable Network Presence: S7 traffic is easy to recognize (port 102, ISO-on-TCP), making it visible via tools like Wireshark, Zeek, or passive OT platforms such as Claroty or Nozomi.
- Security Platform Integration: Modern OT monitoring solutions increasingly support deep-packet inspection of S7, enabling threat detection and auditability.
- Predictable Behavior: S7 communications follow regular polling intervals, allowing behavioral baselining for anomaly detection.
❌ The Cons: Where S7 Falls Short in Cyber Defense
However, S7 was never designed with security in mind — and that's where risk emerges:
- No Native Encryption or Authentication → S7 traffic is in plaintext, opening the door for MITM attacks, unauthorized commands, and configuration tampering.
- Legacy Vulnerabilities → Older implementations are still widely deployed — and susceptible to replay attacks, DoS exploits, and spoofing.
- Patching Challenges → PLC firmware updates can be disruptive, meaning many vulnerable assets remain unpatched for years.
- Complex Topologies → Poor documentation and dynamic environments make it harder for ASM tools to map out all asset relationships, especially if S7 spoofing is involved.
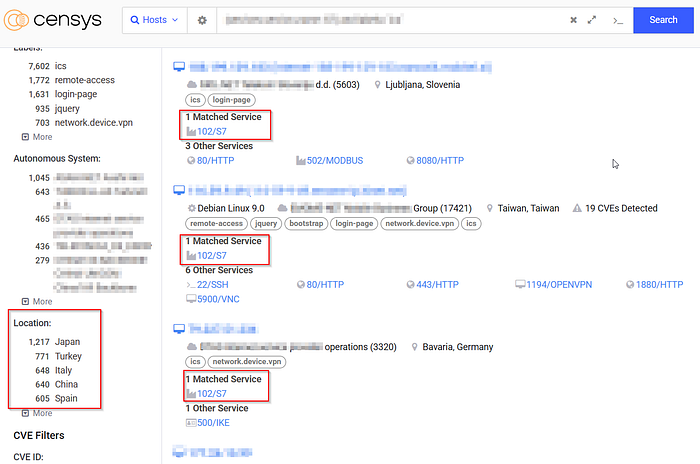
📊 Field Data Insight
According to my recent analysis, over 7,600 S7 endpoints were detected globally — with a significant concentration in Japan. Alarmingly, 589 of these devices are associated with known exploits, underscoring the urgency of better asset visibility and security hygiene in these environments.
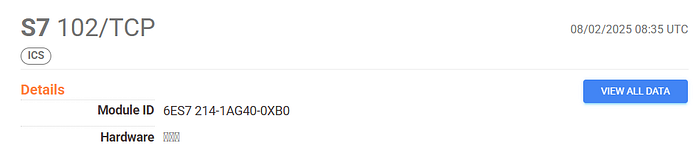
🧩 What Can Security Teams Do?
Area Best Practice Asset Discovery Use passive monitoring tools with native S7 support. Segmentation Isolate S7 zones with strict ACLs; block unauthorized port 102 traffic. Behavioral Monitoring Baselining S7 comms helps spot anomalies like rogue write operations or command abuse. Protocol Whitelisting Only permit trusted HMI/PLC pairs to communicate via S7. Firmware Management Maintain an up-to-date inventory of firmware versions and known vulnerabilities. Security Gateways Deploy industrial firewalls or DPI tools to control and inspect S7 traffic at the perimeter.
🔐 Final Thoughts
The S7 protocol remains a cornerstone of industrial operations — but its design reflects a pre-cybersecurity era. While its consistency aids ASM workflows, the lack of native security controls, especially in legacy systems, creates significant exposure.
Visibility is possible. Defensibility is achievable. But only if organizations treat protocols like S7 as both an asset and a threat surface.
This research part of oaps_another_attack_surface series, another interesting blog about industrial exposed: MMS And you found me LinkedIn , support palestine.
