Hello everyone! I'm Maseera Fatima, a final-year B.Tech CSE student passionate about blue teaming. In this blog, I'll be solving Search Skills. Let's get started!
Task 2: Evaluation of Search Results
Ques: What do you call a cryptographic method or product considered bogus or fraudulent?
Ans: Snake Oil
Ques: What is the name of the command replacing netstat in Linux systems?
Ans: ss
Task 3: Search Engines
Ques: How would you limit your Google search to PDF files containing the terms cyber warfare report?
Ans: filetype:pdf cyber warfare report
Ques: What phrase does the Linux command ss stand for?
Ans: Socket Statistics
Task 4: Specialized Search Engines
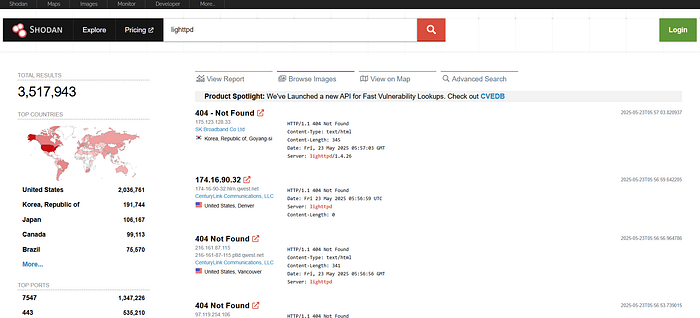
Ques: What is the top country with lighttpd servers?
Ans: United States
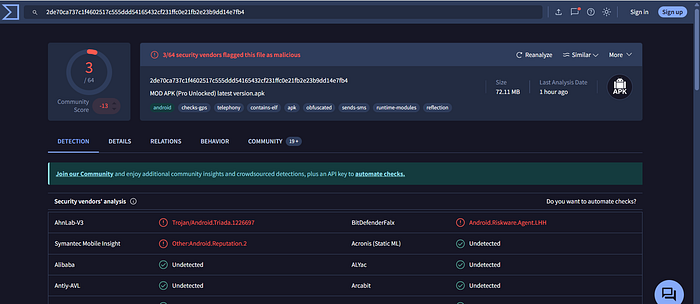
Ques: What does BitDefenderFalx detect the file with the hash 2de70ca737c1f4602517c555ddd54165432cf231ffc0e21fb2e23b9dd14e7fb4 as?
Ans: Android.Riskware.Agent.LHH
Task 5: Vulnerabilities and Exploits
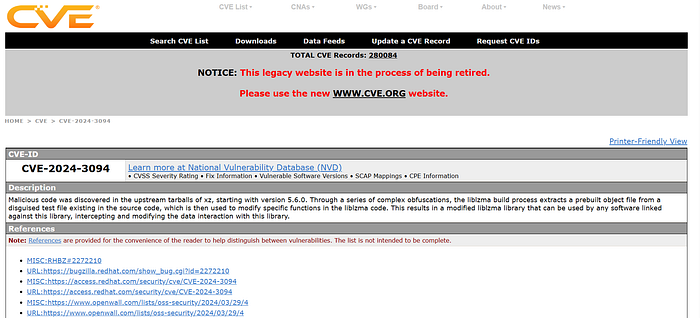
Ques: What utility does CVE-2024–3094 refer to?
Ans: xz
Task 6: Technical Documentation
Ques: What does the Linux command cat stand for?
Ans: concatenate
Ques: What is the netstat parameter in MS Windows that displays the executable associated with each active connection and listening port?
Ans: -b
Task 7: Social Media
Ques: You are hired to evaluate the security of a particular company. What is a popular social media website you would use to learn about the technical background of one of their employees?
Ans: LinkedIn
Ques: Continuing with the previous scenario, you are trying to find the answer to the secret question, "Which school did you go to as a child?". What social media website would you consider checking to find the answer to such secret questions?
Ans: Facebook
Thank you for reading till the end! Stay tuned for the next blog — see you there!