In this article i will show you how to hide shell commands inside image files and how to run them, the purpose of this article is not to do something malicious but learn something fun, lets start!
How it works
jpg images have a metadata section that is used by the cameras to store information related to the file, also programs like photoshop and GIMP can use them, those fields can be exploited in order to place our commands or even small binaries and then retrieve them and execute them.
Get an image
We will download this harmless kitten from Wikipedia. We will use this image for our experiments and see how a cute kitten can transform to a Panther coming out of the shadows!
wget https://upload.wikimedia.org/wikipedia/commons/b/bc/Juvenile_Ragdoll.jpg -O kitten.jpgEmbedding shell commands in the metadata of the image
First we need to install exiftool which allows to manipulate the metadata of a jpg file. to install this on Ubuntu enter
$ sudo apt-get install exiftoolNow enter the following
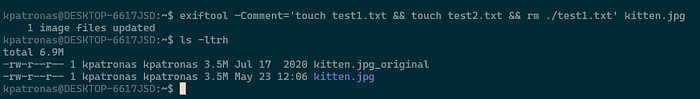
$ exiftool -Comment='touch test1.txt && touch test2.txt && rm ./test1.txt' kitten.jpgThis command writes the following command to the "Comment" metadata field
touch test1.txt && touch test2.txt && rm ./test1.txtThe exit command will keep a backup of the original command
How to execute the commands within the image
To execute the commands you need a combination of exiftool and eval , the first one extracts the the "Comment" metadata and the second one executes the metadata text as shell commands
$ eval "$(exiftool -Comment kitten.jpg | cut -d':' -f2-)"Lets break down this command to understand how it works
running exiftool -Comment kitten.jpg returns the following line
$ exiftool -Comment kitten.jpg
Comment : touch test1.txt && touch test2.txt && rm ./test1.txtThen the result is piped to the cut command which keeps everything after ":"
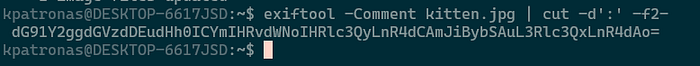
$ exiftool -Comment kitten.jpg | cut -d':' -f2-
touch test1.txt && touch test2.txt && rm ./test1.txtAnd lastly the eval command executes the command, we can see that generated files test1.txt and test2.txt and deleted test1.txt
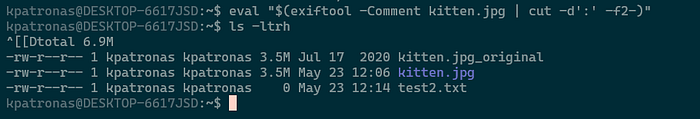
We are sure that file test1.txt created and deleted because test2.txt is executed only upon successful execution of first command because of &&
How to hide the shell commands
If we want to hide commands before execution the simplest one is to base64 encode them and decode them on the fly upon eval execution. The following command embeds the commands as base64 strings
$ exiftool -Comment="$(echo 'touch test1.txt && touch test2.txt && rm ./test1.txt' | base64)" kitten.jpg
1 image files updatedWe can verify that the commands are exists as base64 strings with the exiftool command
How to decode the hidden shell commands and execute them
To decode and execute the base64 encoded commands from the "Comment" metadata field enter the following
eval "$(exiftool -Comment kitten.jpg | cut -d':' -f2- | tr -d ' ' | base64 -d)"The command is quite similar with the eval command in the previous example but with two additions
tr -d ' 'which deletes any spaces that might mess our input.base64 -dwhich decodes the base64 strings back to readable format.
A challenge for you!
Can you find a way of grow to embed an actual shell script file in the metadata? let me know in the comments!
Conclusion
This small article probably does not have any real life applications but can show you how to make some nice tricks to have fun and impress your geeky friends! :)
